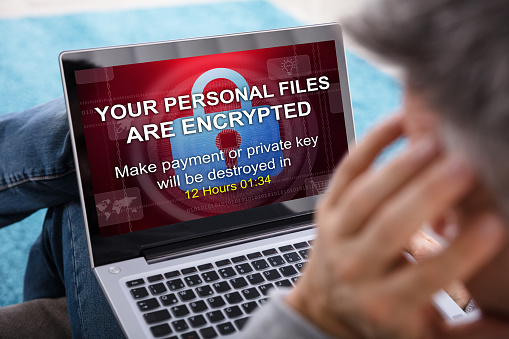
Feeling The Love?
There is a lot to love about the work that you do, and hopefully, your technology is part of that. Loving your IT means having a great relationship not only with the devices, software, and applications you use each day, but with the folks who look after them. If you’ve stopped feeling that spark…